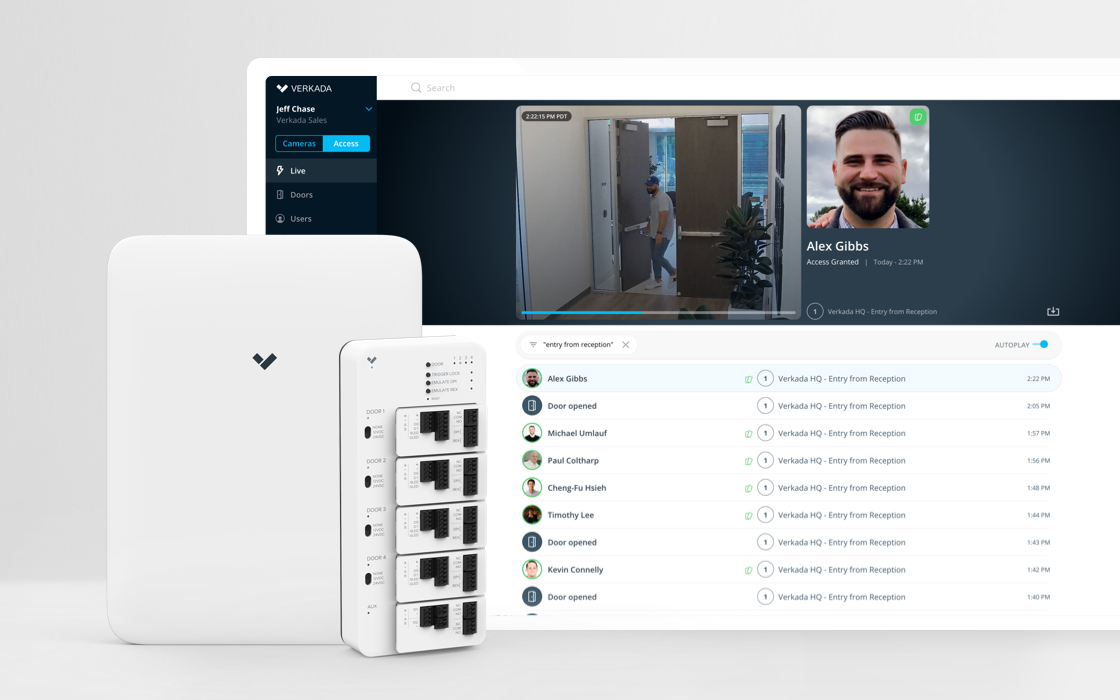
Access control is a vital part of information security and is defined as the process by which you grant or deny access to your data, property, and other objects. Three elements make up access control: identification, authentication, and authorization.
The world of information security is vast.